Sensitive data in logs
When was the last time you checked your logs for sensitive data?
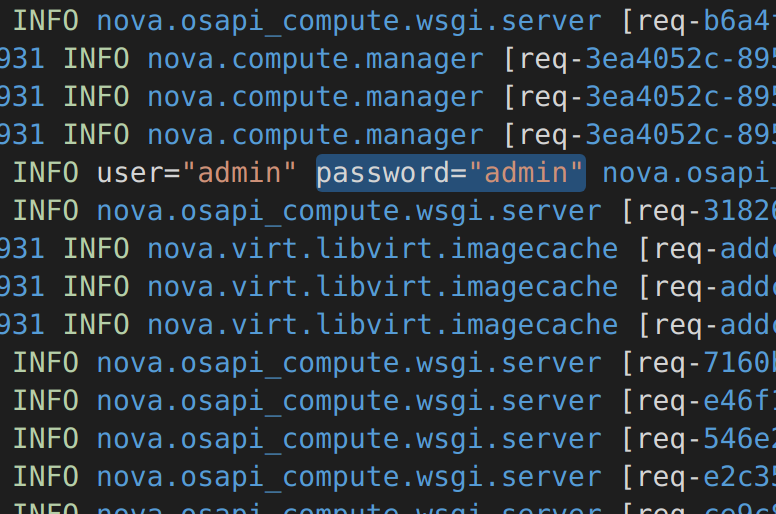
Maybe never, only you know that.
Problem
Log files may be full of very usefull information. Useful for you … and well for bad actors as well. Those could contain passwords, secret keys, tokens, PII and so on.
It is not only a best practice to not have sensitive data in logs but also a requiment that you probably have to comply with.
Solution
To solve this problem I created a simple python script that uses regex patterns under the hood. It will check logs for passwords and various secrets.
You can find it here: Log-Scan
Simply clone the repo to your machine. And run the script python3 log-scan.py -l log.log
There is a patterns.txt file that contains varios regex pattersn like PASSWORD[=:](.*) or secret[=:](.*). You can add other patterns as you wish.
If any sensitive data is found results folder will be created with json result file that will show all the findings.
{
"file": "log.log",
"findings": [
{
"pattern": "assword[=:](.*)\n",
"match": "assword=\"admin\" user=\"admin\" role=\"Administrator\"\n",
"line number": "6",
"line": "password=\"admin\" user=\"admin\" role=\"Administrator\"\n"
},
{
"pattern": "token[=:](.*)\n",
"match": "token=\"2sd43dh4kf54e56f5lv4xsf6546\"\n",
"line number": "29",
"line": "file=\"adword.sh\" token=\"2sd43dh4kf54e56f5lv4xsf6546\" action=\"send\"\n"
}
]
}